Cyclone Update: Depression Likely Over Bay Of Bengal Today
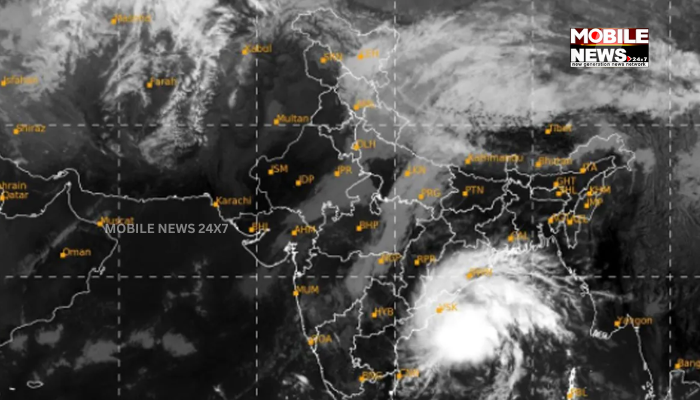
Bhubaneswar: The Well Marked Low Pressure Area over North Andaman Sea and adjoining Southeast Bay of Bengal now lies over Southeast Bay of Bengal and adjoining areas of Eastcentral Bay of Bengal & north Andaman sea.
It is very likely to move northwestwards and concentrate into a Depression over Eastcentral & adjoining Southeast Bay of Bengal today during the next 12 hours and then moving northwestwards, intensify further into a Deep Depression over Eastcentral and adjoining Southeast & Westcentral Bay of Bengal on October 23.
Subsequently, it is very likely to recurve gradually northwards and intensify into a Cyclonic Storm over Westcentral & adjoining Eastcentral Bay of Bengal by October 24th. Thereafter, it is likely to move north-northeastwards and reach near West Bengal-Bangladesh coasts by the morning of 25th October, skirting Odisha coast.
Under the influence of the above system, scattered to fairly widespread light/moderate rainfall with isolated heavy falls is very likely over Odisha during October 23-25. Isolated very heavy rainfall is also very likely over Odisha on October 24.